Adding the Content-Security-Policy HTTP header to a web page and providing settings to restrict what resources the user agent is authorized to load for that page is the process of configuring Content Security Policy. A page that uploads and shows photographs, for example, may accept images from anywhere but limit form actions to a single endpoint. A well-designed Content Security Policy can help protect a page from cross-site scripting. This article demonstrates how to correctly write such headers and includes examples.
A default-src policy directive should be included in your policy as a fallback for other resource types that don't have their own rules. To prohibit inline scripts from running, a policy must include a default-src or script-src directive, as well as the use of eval(). To prevent inline styles from being applied from a <style> element or a style attribute, a policy must include a default-src or style-src directive.
You must configure your web server to return the Content-Security-Policy HTTP header in order to enable CSP in a Drupal site. To enable and configure, download the Content security policy module or use composer: $ composer require 'drupal/csp:1.16'. After installing the drupal module, enable the CSP module in the module page.
The safest approach to configure Content Security Policy without affecting the website is to enable "Report-only." This allows you to see which elements would not be loaded if the policy was activated through your web browser or automatically generated reports.
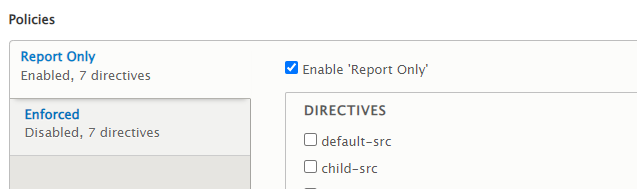
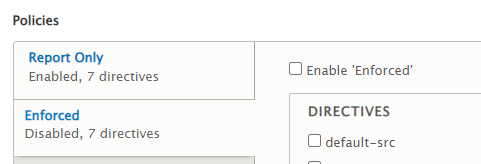
And Click the Enforced tab in your Content Security Policy module settings once all problems have been fixed.
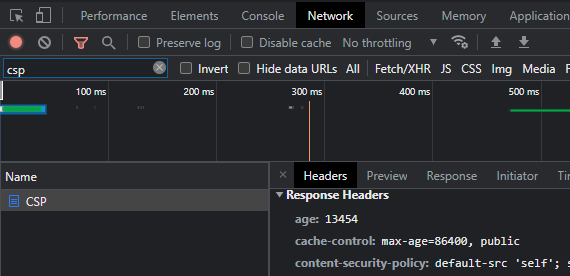
To check content if the Content-Security-Policy is successfully added on HTTP header, go to network tab check response header.
You can also use a command line or script to transfer data, CURL. In your terminal input this following command:
curl –head <site url>
THREATS
Mitigating cross-site scripting
Preventing and reporting XSS attacks are the CSP's main purpose. XSS attacks take advantage of the browser's faith in the content received from the server. Malicious scripts are executed by the victim's browser because the browser trusts the source of the content, even when it's not coming from where it seems to be coming from.
Mitigating packet sniffing attacks
A server can indicate which protocols are allowed to be used; for example, a server can specify that all content must be loaded via HTTPS (which is desirable from a security aspect). A comprehensive data transmission security plan comprises not only requiring HTTPS for data transfer, but also adding the secure attribute to all cookies and providing automatic redirects from HTTP to HTTPS URLs. Sites can also use the Strict-Transport-Security HTTP header to force browsers to connect to them via an encrypted channel.
References:
https://www.inmotionhosting.com/support/edu/drupal/content-security-policy-csp-drupal-8/
https://developer.mozilla.org/en-US/docs/Web/HTTP/CSP